SOC 2 and the SaaS Journey
SaaS leaders prioritize two things: Trust, and Data Security
As SaaS solutions power modern business operations, customers are more concerned than ever about how their data is managed. This is where SOC 2 compliance comes into play-offering a way for SaaS companies to prove they handle customer data securely, gaining trust and credibility.
SOC 2 (System and Organization Controls 2) certification demonstrates that a company has effective controls in place to safeguard customer data. It's not just about meeting standards; it's about adopting best practices that keep your business secure and competitive.
When Should a SaaS Company Consider SOC 2 Certification?
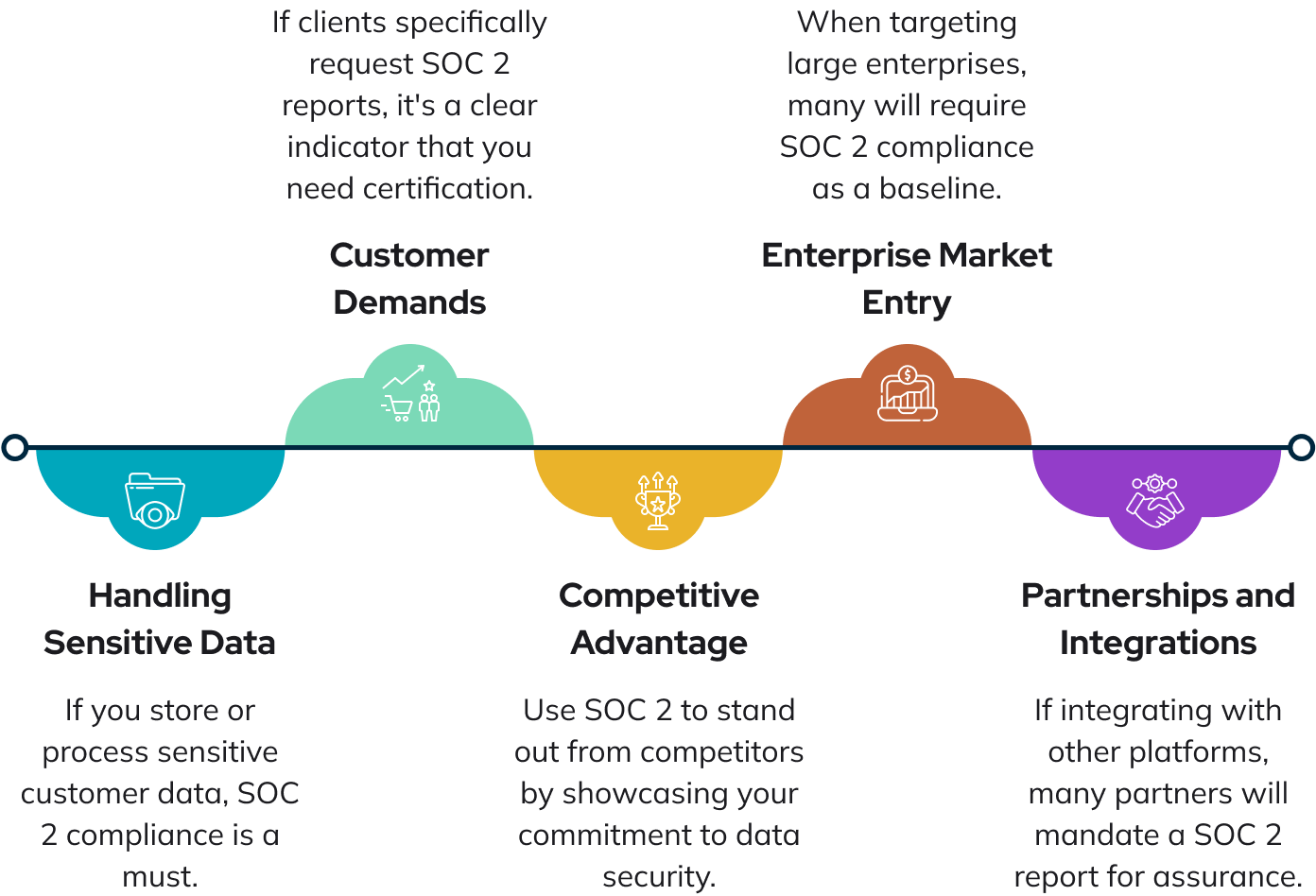
What Does It Take for a SaaS Company to Achieve SOC 2 Certification?
SOC 2 compliance involves a structured process focusing on security, integrity, availability, confidentiality, and privacy. Here’s a step-by-step checklist to guide you through the process:
Checklist for Achieving SOC 2 Compliance
1. Preparation & Planning
2. Infrastructure & Security Controls
3. Documentation & Policies
4. Conduct a Gap Analysis
5. Implement & Test Controls
6. Employee Training & Awareness
7. Engage an External Auditor
8. External Audit Process
9. Review & Certification
10. Ongoing Compliance & Monitoring
SOC 2 compliance is not just a one-time effort but an ongoing commitment to data security and privacy.






Your email address will not be published. Required fields are marked *